RC4信息泄露漏洞原理
时间:2020-10-29 19:44 来源:潇湘夜雨 作者:华嵩阳 点击:次
| 一、简介 2015年3月26日,国外数据安全公司Imperva的研究员Itsik Mantin在BLACK HAT ASIA 2015发表论文《Attacking SSL when using RC4》阐述了 利用存在了13年之久的RC4漏洞——不变性弱密钥(《Weakness in the Key Scheduling Algorithm of RC4》,FMS 发表于2001年)进行的攻击,并 命名为“受戒礼”攻击(Bar Mitzvah Attack)。 直到2015年3月,还有约30%的网络通信是由RC4进行保护的。通过“受戒礼”攻击,攻击者可以在特定环境下只通过嗅探监听就可以还原采用RC4保护 的加密信息中的纯文本,导致账户、密码、信用卡信息等重要敏感信息暴露,并且可以通过中间人(Man-in-the-middle)进行会话劫持。 二、扫描验证 系统环境:centos、redhat 1、安装openssl yum -y install openssl 2、命令扫描 #验证RC4算法
[root@web ~]# openssl s_client -connect www.taobao.com:443 -cipher RC4
CONNECTED(00000003)
140545796552520:error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert handshake failure:s23_clnt.c:744:
---
no peer certificate available #返回结果无证书信息,说明服务端口没有使用RC4加密算法
---
No client certificate CA names sent
---
SSL handshake has read 7 bytes and written 133 bytes
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
---
#验证SHA加密算法
[root@web ~]# openssl s_client -connect www.taobao.com:443 -cipher SHA
CONNECTED(00000003)
depth=2 C = BE, O = GlobalSign nv-sa, OU = Root CA, CN = GlobalSign Root CA
verify return:1
depth=1 C = BE, O = GlobalSign nv-sa, CN = GlobalSign Organization Validation CA - SHA256 - G2
verify return:1
depth=0 C = CN, ST = ZheJiang, L = HangZhou, O = "Alibaba (China) Technology Co., Ltd.", CN = *.tmall.com
verify return:1
---
Certificate chain #返回了正式信息,说明支持SHA算法
0 s:/C=CN/ST=ZheJiang/L=HangZhou/O=Alibaba (China) Technology Co., Ltd./CN=*.tmall.com
i:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2
1 s:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2
i:/C=BE/O=GlobalSign nv-sa/OU=Root CA/CN=GlobalSign Root CA
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIJHTCCCAWgAwIBAgIMbVVxYu+0omQQP3O4MA0GCSqGSIb3DQEBCwUAMGYxCzAJ
BgNVBAYTAkJFMRkwFwYDVQQKExBHbG9iYWxTaWduIG52LXNhMTwwOgYDVQQDEzNH
bG9iYWxTaWduIE9yZ2FuaXphdGlvbiBWYWxpZGF0aW9uIENBIC0gU0hBMjU2IC0g
RzIwHhcNMjAwOTI3MDYzMjAyWhcNMjExMDI5MDYyNjAzWjB4MQswCQYDVQQGEwJD
TjERMA8GA1UECBMIWmhlSmlhbmcxETAPBgNVBAcTCEhhbmdaaG91MS0wKwYDVQQK
EyRBbGliYWJhIChDaGluYSkgVGVjaG5vbG9neSBDby4sIEx0ZC4xFDASBgNVBAMM
CyoudG1hbGwuY29tMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAE47F4GZz0WqTM
BlUlMRsav9Q236UNl6gyUX5A834ygyAqYBnKgn+Ch6NceVuw82n9OPZJGbKXekex
LvdgOM5N9aOCBoIwggZ+MA4GA1UdDwEB/wQEAwIDiDCBoAYIKwYBBQUHAQEEgZMw
gZAwTQYIKwYBBQUHMAKGQWh0dHA6Ly9zZWN1cmUuZ2xvYmFsc2lnbi5jb20vY2Fj
ZXJ0L2dzb3JnYW5pemF0aW9udmFsc2hhMmcycjEuY3J0MD8GCCsGAQUFBzABhjNo
dHRwOi8vb2NzcDIuZ2xvYmFsc2lnbi5jb20vZ3Nvcmdhbml6YXRpb252YWxzaGEy
ZzIwVgYDVR0gBE8wTTBBBgkrBgEEAaAyARQwNDAyBggrBgEFBQcCARYmaHR0cHM6
Ly93d3cuZ2xvYmFsc2lnbi5jb20vcmVwb3NpdG9yeS8wCAYGZ4EMAQICMAkGA1Ud
EwQCMAAwSQYDVR0fBEIwQDA+oDygOoY4aHR0cDovL2NybC5nbG9iYWxzaWduLmNv
bS9ncy9nc29yZ2FuaXphdGlvbnZhbHNoYTJnMi5jcmwwggOyBgNVHREEggOpMIID
pYILKi50bWFsbC5jb22CCiouMTY4OC5jb22CDiouM2MudG1hbGwuY29tgg0qLmFs
aWJhYmEuY29tghAqLmFsaWV4cHJlc3MuY29tghIqLmFsaXFpbi50bWFsbC5jb22C
DSouYWxpdHJpcC5jb22CDCouYWxpeXVuLmNvbYINKi5jYWluaWFvLmNvbYIQKi5j
YWluaWFvLmNvbS5jboIQKi5jaGkudGFvYmFvLmNvbYIPKi5jaGkudG1hbGwuY29t
ghIqLmNoaW5hLnRhb2Jhby5jb22CDiouZGluZ3RhbGsuY29tggoqLmV0YW8uY29t
ggsqLmZlaXpodS5jboIMKi5mZWl6aHUuY29tggwqLmZsaWdneS5jb22CCyouZmxp
Z2d5LmhrghAqLmZvb2QudG1hbGwuY29tghAqLmppYS50YW9iYW8uY29tgg8qLmpp
YS50bWFsbC5jb22CDyouanUudGFvYmFvLmNvbYIPKi5qdWh1YXN1YW4uY29tgg8q
Lmx3LmFsaWltZy5jb22CDCoubS4xNjg4LmNvbYIPKi5tLmFsaWJhYmEuY29tgg8q
Lm0uYWxpdHJpcC5jb22CDyoubS5jYWluaWFvLmNvbYIMKi5tLmV0YW8uY29tgg4q
Lm0udGFvYmFvLmNvbYITKi5tLnRhb3BpYW9waWFvLmNvbYINKi5tLnRtYWxsLmNv
bYIMKi5tLnRtYWxsLmhrghEqLm0ueWFvLjk1MDk1LmNvbYIJKi5tZWkuY29tggwq
LnRhb2Jhby5jb22CESoudGFvcGlhb3BpYW8uY29tggoqLnRtYWxsLmhrghEqLnRy
aXAudGFvYmFvLmNvbYILKi54aWFtaS5jb22CDyoueWFvLjk1MDk1LmNvbYIIMTY4
OC5jb22CC2FsaWJhYmEuY29tgg5hbGlleHByZXNzLmNvbYILYWxpdHJpcC5jb22C
CmFsaXl1bi5jb22CC2NhaW5pYW8uY29tgg5jYWluaWFvLmNvbS5jboIMZGluZ3Rh
bGsuY29tgghldGFvLmNvbYIJZmVpemh1LmNuggpmZWl6aHUuY29tggpmbGlnZ3ku
Y29tgglmbGlnZ3kuaGuCDWp1aHVhc3Vhbi5jb22CEW0uaW50bC50YW9iYW8uY29t
ggdtZWkuY29tggp0YW9iYW8uY29tgg90YW9waWFvcGlhby5jb22CCHRtYWxsLmhr
ggl4aWFtaS5jb22CCXRtYWxsLmNvbTAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYB
BQUHAwIwHwYDVR0jBBgwFoAUlt5h8b0cFilTHMDMfTuDAEDmGnwwHQYDVR0OBBYE
FID1VDod2aq8+TL8VssbHyqXc1AzMIIBBAYKKwYBBAHWeQIEAgSB9QSB8gDwAHYA
7sCV7o1yZA+S48O5G8cSo2lqCXtLahoUOOZHssvtxfkAAAF0zkLqSQAABAMARzBF
AiB/nK13u8kYP6+iRqwRSMqn78zDc0AibXVMDA2s3EyAYgIhALPy7DzDfn8inJip
WN5SDhVgNruLZ7sMzBepydpGwTBlAHYA9lyUL9F3MCIUVBgIMJRWjuNNExkzv98M
LyALzE7xZOMAAAF0zkLqJwAABAMARzBFAiEA1TUuzf71N/6841oRag7EszN5+sWA
CPl5cVZGXwiUMPkCIHqBqmLThrrTFhlVE+/Z3CbvIH5e68oy4c+YWAf0CNdgMA0G
CSqGSIb3DQEBCwUAA4IBAQCIitPKdkKuzg5Piz4FEVeqr2C/Lhp+yd5QLMDGX4NV
hovLlCAqOW/HxBwyy8DJn/8sgKY2+eOO7b/z+40cIEJKlkZtONDKz1uFZZpuc6K7
caNn87PNxC0l8AfTtfi+e+OIyVrp6xygKIzsNRJTMvJXbXMXKQXR4k8erkyaRpDc
G+oUNt+6xBS+01kXPQvH5V5KUZt5YIhPl7pd36cYkvWVhNAPTzIhUBqMYRfFfc7r
rc6xUkdAP77JwDGHAs3kPSJKbin68D4wja+5fPW8PC+vscPHwSJVHjsj6uVR4Wv4
OsSaPP+C9HsAvWP284Zi7xbb0PckT+i7slGJJ4nHaGpG
-----END CERTIFICATE-----
subject=/C=CN/ST=ZheJiang/L=HangZhou/O=Alibaba (China) Technology Co., Ltd./CN=*.tmall.com
issuer=/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2
---
No client certificate CA names sent
Server Temp Key: ECDH, prime256v1, 256 bits
---
SSL handshake has read 3966 bytes and written 371 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-ECDSA-AES128-SHA
Server public key is 256 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-ECDSA-AES128-SHA
Session-ID: F1D73BD2560E0FB7664E7769BBECC44FF0E1DF34579EB26403337160A2394D08
Session-ID-ctx:
Master-Key: DA311100EAE33A47544F743C2646B0D13D56D1B83DC5CCFE6A348E695FCA48130DC076978F841E35C66B943E0A7737B0
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 900 (seconds)
TLS session ticket:
0000 - c7 f3 15 16 ca 6f 94 ed-9e 9e 8e b7 f6 f1 53 b1 .....o........S.
0010 - 8b fa a1 4d d0 8d c2 03-c7 97 81 b8 17 9a 73 bb ...M..........s.
0020 - c7 9c db 22 95 be 80 51-ca 8e ee e7 b2 26 62 ae ..."...Q.....&b.
0030 - 65 ed be f7 1e 73 91 a1-90 20 f4 f2 82 3b ec e7 e....s... ...;..
0040 - 62 81 8b 59 d6 b1 1c 9e-66 ab 93 d6 04 3b 3f 95 b..Y....f....;?.
0050 - e6 f2 9c 5a b2 fe 7a 1a-14 67 ad 66 8f 90 1f 79 ...Z..z..g.f...y
0060 - 4e 75 7a ca 6a fd 8c 22-bf d9 94 c6 8c 6c d1 4d Nuz.j..".....l.M
0070 - 1f 66 3d 5f 32 da 65 3d-68 5c cd dd 9e 0b c1 ee .f=_2.e=h\......
0080 - 81 06 a1 bd 20 52 c7 09-17 b5 c8 f8 79 cc ee da .... R......y...
0090 - 9e fb 4c 28 f5 92 39 a9-76 9f 12 05 8b e3 09 09 ..L(..9.v.......
Start Time: 1603893802
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
closed
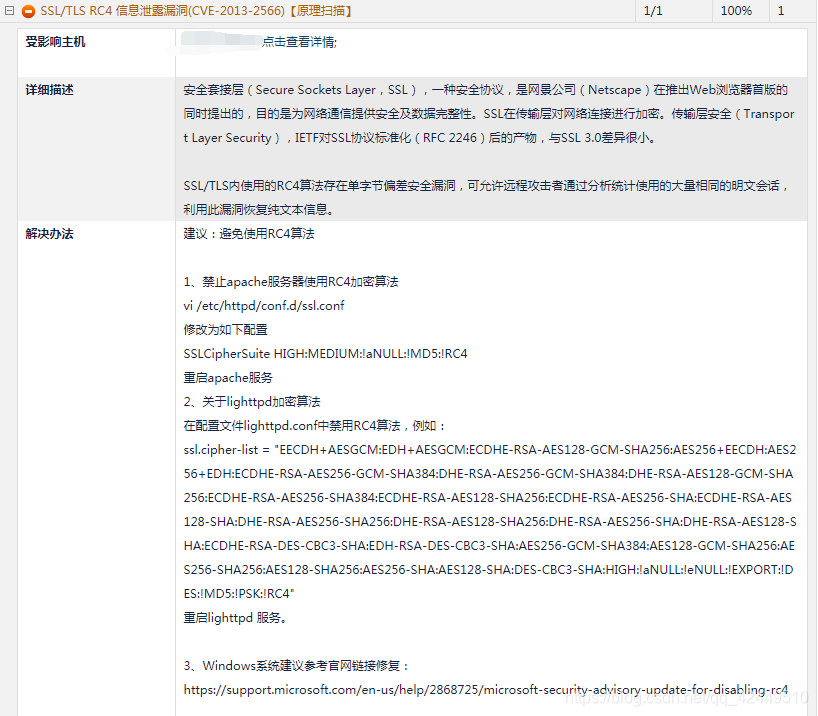
三、解决方案 1、根据各应用服务的官方解决方案关闭RC4算法
结束语: 互联网高速发展的今天,安全问题层出不穷,面对安全问题,我们要客观理性的分析评估,首先要分析漏洞危害的大小、影响范围、利用 (责任编辑:liangzh) |